Owlet Programming Language
National Laboratory for Parallel and Distributed Processing, China
Owlet is an interaction language based on event publish/subscribe communication primitive to specify the interactions among distributed nodes to collect, organize and comprehensively utilize the resources on the Internet. It abstracts the resources as agents, and the interactions are described in terms of different roles of the agents. By using peer-to-peer overlay network and content-based publish/subscribe event service as the enabling technologies, Owlet provides the language constructs that facilitate the construction of large-scale distributed systems by separating its resource aggregation logic and business logic.
We have implemented a prototype of Owlet compiler and its runtime environment. Experiments show that large-scale distributed applications can be elegantly constructed in Owlet, and a high level of fault tolerance and a certain degree of load balancing among networked nodes can be achieved.
The Owlet runtime environment provides necessary mechanisms to support Owlet language constructs. As shown in the figure, it has four layers: the transport layer, the overlay layer, the services layer and the role container layer.
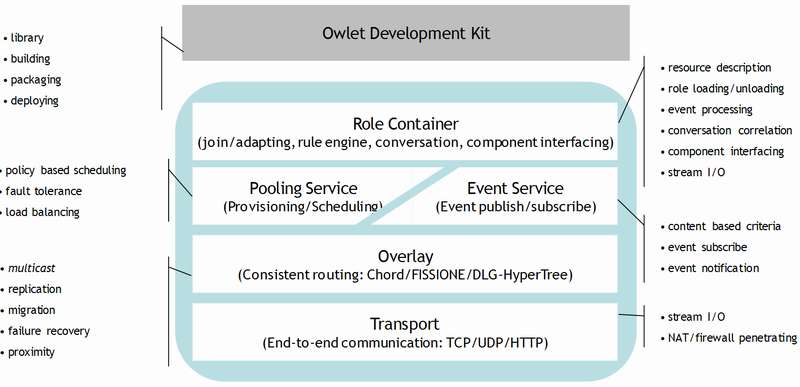
* The overlay layer is provided as another project at http://overlay.sourceforge.net, which also hosts DLG-HyperTree.
Sample Applications
Peer-to-Peer File Sharing
Peer-to-peer file sharing is a typical large-scale distributed applica-tion that uses the idle bandwidth and storage of other nodes to facilitate file transfer in the Internet. It has the advantage of scal-ability even when a large number of nodes are downloading files from one node, because each requesting node will provide a trunk of the file for other requesting nodes when possible. Files are usually split into small pieces, so that different pieces can be fetched from different nodes.
Distributed Prime Checker
A distributed prime number checking program is built using Owlet. To reflect the autonomous and dynamic nature of resources on the Internet, we inject random behaviors into the checking program so that about 40% of the checking processes will fail.
Related Papers
Visitors
